CERT-SE CTF 2023 Write-up
Description
This year, too, CERT-SE has a challenge (CTF) during the cyber security month. This challenge is aimed at anyone with an interest in IT security.
<scenario>
CERT-SE has come across files from an unknown fictional group of defenders of a network. In these files there's "flags" hidden.
Can you find all the flags?
</scenario>
In the .zip file below there is a network dump (PCAP) and a document that contains a total of seven flags, these have the format “CTF[xxxxxxxxxx]”.
Solution
PCAP
IRC Data
In the PCAP, we can find an IRC conversation between three people. Alice, Bob, and Christina.
<Alice>:is this really safe, I mean it's not encrypted right?
<Bob>:we should be safe, it's only internal traffic on the hypervisor
<Bob>:and the secret management system is encrypted with TLS
<Alice>:should we proceed then?
<Bob>:yes, you have to unlock the vault with the secret stored on the secret-management server
<Alice>:yes I know I know. Just give me a sec
<Bob>:ok
<Alice>:so, I have unlocked the vault, you can do your thing now
<Bob>:thanks
<Alice>:Hey, by the way you were saying we are listed on some target list for cyber attacks?
<Bob>:yes we should keep our eyes open for anomalies
<Alice>:ok, I will ping Christina, she is really good with the FPC and the analysis backend
<Bob>:yes, that's a really good idea
<Alice>:ping @Christina
<Christina>:Hi Alice, how are you?
<Alice>:just fine, how are you?
<Christina>:o fine, just a lot of work with the new IDS. So many false positives, not really useful right now
<Alice>:I see. Here is something to cheer you up a bit
PRIVMSG Christina :.DCC SEND message.wav 199 0 11888756 47.
PRIVMSG Christina :SHA-256 checksum for message.wav (remote): 4e31cddd5b972ce211770aca79dc2576099ad07c303de805b89604a7bfbc8b4c
:Christina!~user@192.168.0.30 PRIVMSG Alice :.DCC SEND message.wav 3232235550 51991 11888756 47.
<Christina>:hahaha, that was wonderful. Thank you!
<Bob>:Bob mentioned we are on some list of potential cyber operation targets. Please let us know if you find anything suspicious.
<Christina>:yeah sure will. Do you know what kind of list and who's behind the announcement?
<Alice>:He told me the group announcing the list is known to exfiltrate information
<Christina>:ok, I'll see what I can find
<Alice>:Oh no
<Christina>:Looks like they got in to that mail server we told operations to patch weeks ago!!
<Christina>:need to investigate what data they transferred but It looks like it originates from the secret-management server.......
<Alice>:Oh no, Bob and I used the secret earlier today
From this conversation, we now know that there is a secret management server that is protected by TLS. We also know that someone has gained access to their network and has been able to exfiltrate data from the secret management server, and finally, we know that an audio file has been sent from Alice to Christina.
DCC Data
The DCC data is located in TCP stream 54.
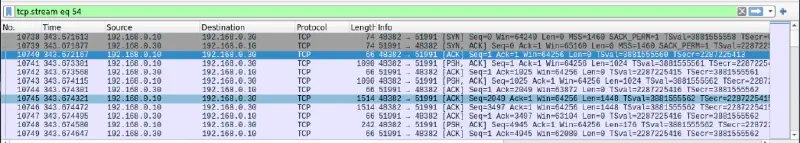
Saving the data being sent in this stream, we get the original file, message.wav, that Alice sent to Christina.
The audio file is a one-minute loop of an 8-bit version of “Never Gonna Give You Up”. But listening closely, something different can be heard in the background around 30 seconds in.
Taking a look at the audio file using a spectrogram, we can see that there is something that looks like a digital signal hidden in the background.

Isolating the frequency, we get the following signal.
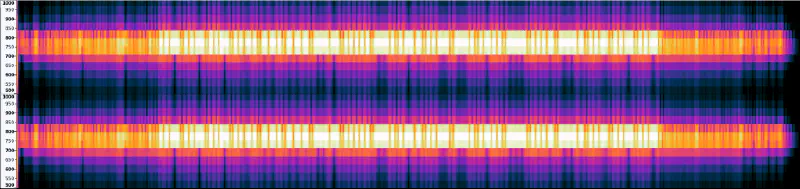
With the help of Sigidwiki, we can identify the signal as a PSK31 signal. With the use of a tool like DigiPan, we can decode the signal.
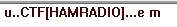
And there we have our first flag.
CTF[HAMRADIO]
Secret-management Server
In the packet capture, we can find a HTTP POST request coming from the Secret-management server.
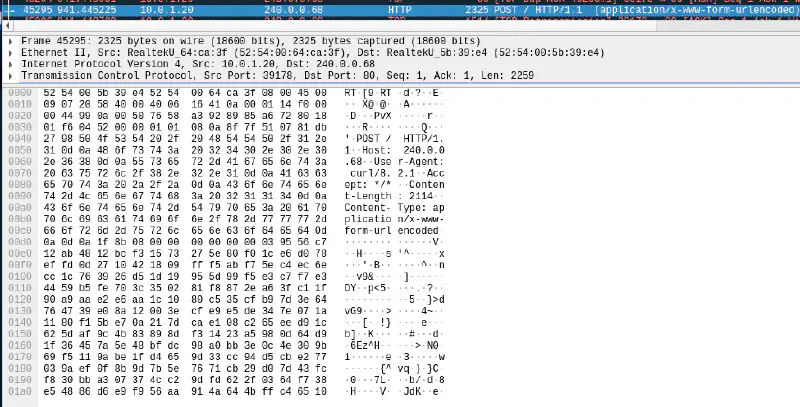
Exporting the POST data, we can see that it’s gzipped.
file post
post: gzip compressed data, from Unix, original size modulo 2^32 2900
After decompressing the data, we get a private key and a certificate.
-----BEGIN PRIVATE KEY-----MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQDU7yGUoAUtql9a9QRcqcL8WLyyEVHbqL/twiO65RRU7mQW47jlUTyAqMYdsDgllnItuqZ2MGIzNCwLqfiN9qlCGQ3NPb0wv/SWxMjxlA12F3Pwz9zLAZfWYB587K7q1cIVI4Ztlk3GAW5CRVjBrNZgt1dGxPH0iGGtoyXtbj3rAuUKim3FMw0U8fx8mRZuR6lqWIT+p2OET01nw+KuCgXRgaYgm2CZQij9VW2YotAByECN+DI6Rxx6FEZJe9/qGO7gbjxPb3/PNlRbHqnsF6LcbYweYcluOg2ovfcNMwIY15J6Wi7/0hbUC7zgbsDnzTbJlVDPHI/bWp3an42qZV/lAgMBAAECggEABNR7dpouS+PMX8KPi6+Lx/rA+v64FItjy8zxJQqQYcB6Pj0CTcIAOpXkJTprp59IQz/I31pHxqFlagqmuUenUrkWmPl7IA7hSYXjXfwjAF2rUwLQChMk7Sdcga5tEFAdeSpyC0HTIqLtK+0pRH67FSdg1YQ0TdJFzvEUtD7212y8iopbYH8aoJC5ty/lZMp9uqoy959s4SLkubMYL+SA1Au4fIqC6o99LpmBo74YB+vY6YrCcCT3ymcUsx4p9W17lI6Hh8DI8HToWqFpn6klikvh+tY+aaTFZT/FooqAgKB2M2npnGqKP2Pi4Tm0jw/jnKtF9qFwxy1THPBJDBGYgQKBgQDtPlzWVx0qaey44GwVOHodgZE75vIK8vWEqL1Eb9kybi9oqMWZYOPcbqjj/bRQt8C0qg0jnG+dtt73+80ECJ49O0YRPl5Huy0LdHeMHHiNbLE9D+WrEdqb0e3/2xa71wAztrdHyNfl7XsuqzxbAtZFg4qSWTX0pEtLvm6d+OuTZQKBgQDlxMMU1hZheCT5O1Ggukr+7lgwdGN5vFdTSPdIVAc6eV6iKgMiJb5G6qhOUrjsJmr+9T0LnpcAIGieylO0h7KhkNFNtBB0PMLIxb56fSF7RypYNAB1sGvWO3eZsNwiW8sWSVmRRRnZURSQI+d0Edy5AmJnOb7QQ2XkEU1eBFcSgQKBgGoALTbPoYZr4YsRKvmoTFeWpq+fFpJxz+VAB6DmYKM5vBEFJ5TKR8Ub5HZJyyEtmPqf6FL6+Jv9M06VwRqGRz2QmFPoC/P827l8hlWh+vMll2NzEOkIhyaL+80PtO6kt8BjaSy3vk9Ldnh5pfP8JoTUqzuMhKEUL1hec8o9h/RJAoGBAIuv4rXxLewV4cyPzqF7gIqaFo1mxO9GnIRqsMONKlPXY7wM9Ji2/4YXtTjgu8H93UChkXpV8RFHorMe6GKxuNzWsRifZv1zzyvGZHYNSuSqsEitXLYwCm9U+fI6/qn4ynADKevSadOfonO7EESVc24az/5XsfTldLWB+1o0I0eBAoGAbkIGr+VAwYOliDl9Ax3XKxqzanzzsmiqZnQ8XoCaKAEIOQOLxy6hyBX/ddRAMH8e0yaG+bBstSBnq0gX4qwgJO3pwnvBeTkERQxS/eR0STnObz/B/M8DUEZZUFpK1hYi/SDEWtQ01yr4UMUqh27QTHToWPWEz246+RekeBUvTEY=-----END PRIVATE KEY----------BEGIN CERTIFICATE-----MIIDRTCCAi0CFEHUfr6q2L765N+4Jo6pnAvbWAlZMA0GCSqGSIb3DQEBCwUAMF8xCzAJBgNVBAYTAlNFMRIwEAYDVQQIDAlTdG9ja2hvbG0xDjAMBgNVBAcMBVNvbG5hMRAwDgYDVQQKDAdDVEYyMDIzMRowGAYDVQQDDBFzZWNyZXQtbWFuYWdlbWVudDAeFw0yMzA4MTAwNjUxNTlaFw0yNDA4MDkwNjUxNTlaMF8xCzAJBgNVBAYTAlNFMRIwEAYDVQQIDAlTdG9ja2hvbG0xDjAMBgNVBAcMBVNvbG5hMRAwDgYDVQQKDAdDVEYyMDIzMRowGAYDVQQDDBFzZWNyZXQtbWFuYWdlbWVudDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANTvIZSgBS2qX1r1BFypwvxYvLIRUduov+3CI7rlFFTuZBbjuOVRPICoxh2wOCWWci26pnYwYjM0LAup+I32qUIZDc09vTC/9JbEyPGUDXYXc/DP3MsBl9ZgHnzsrurVwhUjhm2WTcYBbkJFWMGs1mC3V0bE8fSIYa2jJe1uPesC5QqKbcUzDRTx/HyZFm5HqWpYhP6nY4RPTWfD4q4KBdGBpiCbYJlCKP1VbZii0AHIQI34MjpHHHoURkl73+oY7uBuPE9vf882VFseqewXotxtjB5hyW46Dai99w0zAhjXknpaLv/SFtQLvOBuwOfNNsmVUM8cj9tandqfjaplX+UCAwEAATANBgkqhkiG9w0BAQsFAAOCAQEAFD3ccPkRw91kVM0UXUa+7cuA5jZUpC3qW/CUZ8DFe5WUUKXJWBAWB7FQFy8K+jn5CFaR5aHwFvB70VLL7Qzm5egKID9wxLX9heW79KIw5I2E4N+4MO/rLvejNBkQxdUF5cFJhLa6QnGAZPMcpZy8y/PnxKta8He44Iq9EJcR7Npk/YUEJ0rlAF0E/Mn3ObU6mf+TGLwiP/leGXtWa6hVhnSS0lMA373RAXZtVu+3mnyeQlV7Al/3VPKZSxj1eRP5g/gBtMRlzUQWXfP59znlJWbGVYc+de3E6CYqXhCPrquwAMDcq6H8Y3Vx00FYepOIQaJsXqXg7sPboC7mqk0eXA==-----END CERTIFICATE-----
If we use the private key in Wireshark to decrypt the TLS data for 10.0.1.20:443, we can see that an image named secret.png has been downloaded from the Secret-management server.
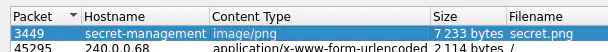
Saving the image and taking a look at it gives us the next flag.

CTF[GALOIS]
FTP-DATA
Taking a look at the other packets in the capture file, we can find an FTP-DATA stream.
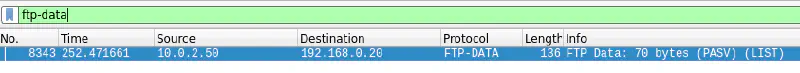
Checking the data transferred, we get the next flag as a file on the FTP server.

CTF[HUNTER2]
Document
There was also a document attached to the challenge. If we open the document we find two images, a number of citations, an excerpt from Shakespeare’s Henry V, and a rebus.

Rebus
Solving the rebus, CTF[☔-ra+💿d=i+⛺t=d], we get the following:
CTF[rain-ra+cd d=i+tent t=d]
CTF[in+cd d=i+tent t=d]
CTF[incitent t=d]
CTF[incident]
CTF[incident]
Logo Image
Opening the CERT-SE logo image in a tool like StegSolve, we get the flag when checking the color planes.
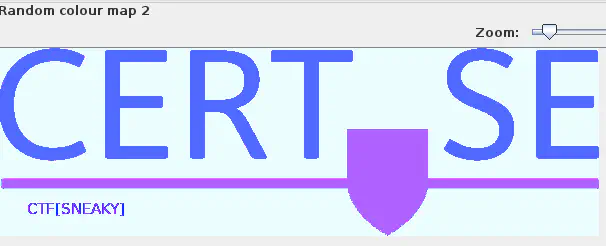
CTF[SNEAKY]
Rock Image
Inspecting the last image in the document, we can see that there is some extra data at the end of the file.
EEEEEEEEEeEEEEeeEEEEEEEEEeEeEeEEEEEEEEEEEeEEEeeEEEEEEEEEEeEeeEeeEEEEEEEEEeEEEEeEEEEEEEEEEeeEeeEEEEEEEEEEEeeeEeEeEEEEEEEEEeeEEeeEEEEEEEEEEeeEEeeE EEEEEEEEEeEEEEeeEEEEEEEEEeeEeEEeEEEEEEEEEeeeEeEEEEEEEEEEEeeeeEEeEEEEEEEEEeEeeeEe
With the help of CyberChef, we can identify this string as a Cetacean Cipher, and decode it to give us the flag.
CTF[Bluff City]
Exif Data
To get the last flag, we have to check the metadata of the document using a tool like exiftool.
ExifTool Version Number : 12.40
File Name : CERT-SE_CTF2023 - CompetenceLateRoadThink.odt
Directory : .
File Size : 218 KiB
File Modification Date/Time : 2023:08:17 12:55:18+02:00
File Access Date/Time : 2023:09:29 09:25:21+02:00
File Inode Change Date/Time : 2023:09:29 08:50:44+02:00
File Permissions : -rw-r--r--
File Type : ODT
File Type Extension : odt
MIME Type : application/vnd.oasis.opendocument.text
Creation-date : 2023:08:08 10:57:12.998681141
Date : 2023:08:09 09:22:24.583354797
Editing-duration : PT21M33S
Editing-cycles : 5
Generator : LibreOffice/7.0.4.2$Linux_X86_64 LibreOffice_project/00$Build-2
Document-statistic Table-count : 0
Document-statistic Image-count : 2
Document-statistic Object-count : 0
Document-statistic Page-count : 2
Document-statistic Paragraph-count: 7
Document-statistic Word-count : 307
Document-statistic Character-count: 1525
Document-statistic Non-whitespace-character-count: 1222
User-defined Name : CTF
User-defined : CTF[WILLIAM]
Preview PNG : (Binary data 8722 bytes, use -b option to extract)
In the property User-defined, we get the last flag.
CTF[WILLIAM]